Hi,
In this post i again try to start the system malware analyse by experimenting in the virtual environment. I hope you may have fun. I think system malware is a vast chapter which may take more patience in order to find fun in that. I hope that there will be more posting regarding the system malware.
Happy hunting :-)
In malware analysis we mostly find the infected binary and try to analyse the source and determine what it exactly to the environment and how much damage occur because of that.
After this preliminary step we create a signature to stop its attack in the future.
There are two signature methods.
- Host-based signature - Identify the files changed on that particular time of infection.
- Netwrok signature - Network traffic will be monitored for finding malware.
These are the techinques used in the Malware Analysis Phase.
- Basic Static Analysis - Examining exe without running it. This method is mostly ineffective.
- Basic Dynamic Analysis - Running the malware in secure environment and get some signature from that. It doesnt need deep programming knowledge. Hence some functionlity malware will be missed.
- Advanced Static Analysis - Reverse engineering the malware internals by loading the exe in disassembler and anlyse the instruction what is does. It should need knowledge of disassembly, windows OS concepts.
- Advanced Dynamic Analysis - Using Debugger to analyse the internal of malicious exe.
There are some common terminology given to malware in the real world environment. It might helpful in narrow down our finding if we know what malware will do in the real worl environment.
- Backdoor - Helps attacker to access the victim machine
- Botnet - These machines are zombies. Which are used to perform DDOS attack.
- Downloader - It will download other malicous code.
- Rootkit - It makes the other malware undetectale. When it is combined with backdoor it is difficult the backdoor in the system.
- Worm or virus - Code that copy itself and infect additional computers.
BASIC STATIC ANALYSIS
In static we ananlyse the malware without actually executing it in the real world environment by using previous hashes, antivirus tools, analysing files strings, functions and headers.
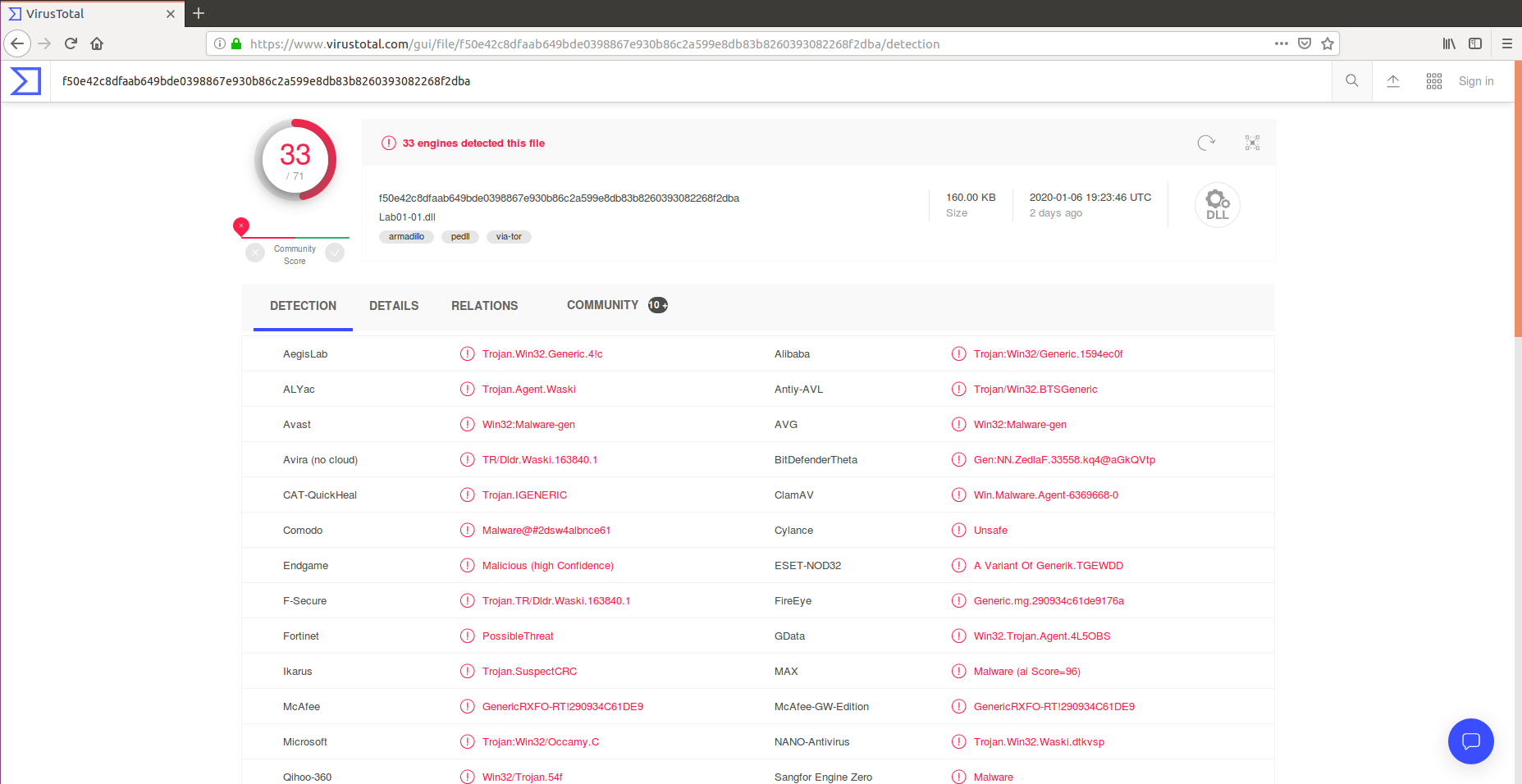
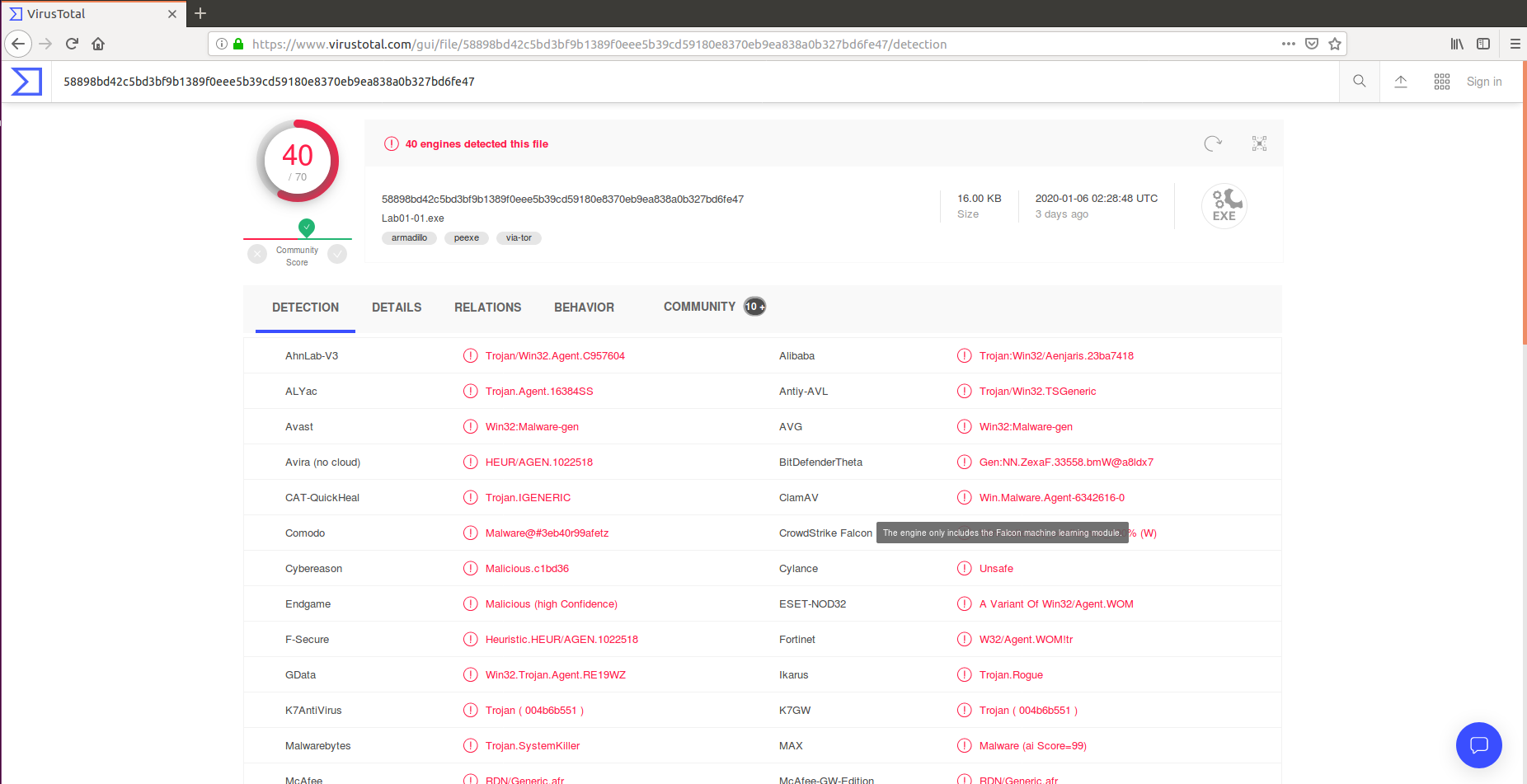
Virustotal
Virustotal is one of the best online tool to identify whether a file is malware or not based on set of malware database.
Below mentioned is the Lab exercise of the first chapter (LAB01-01)
Hash Value
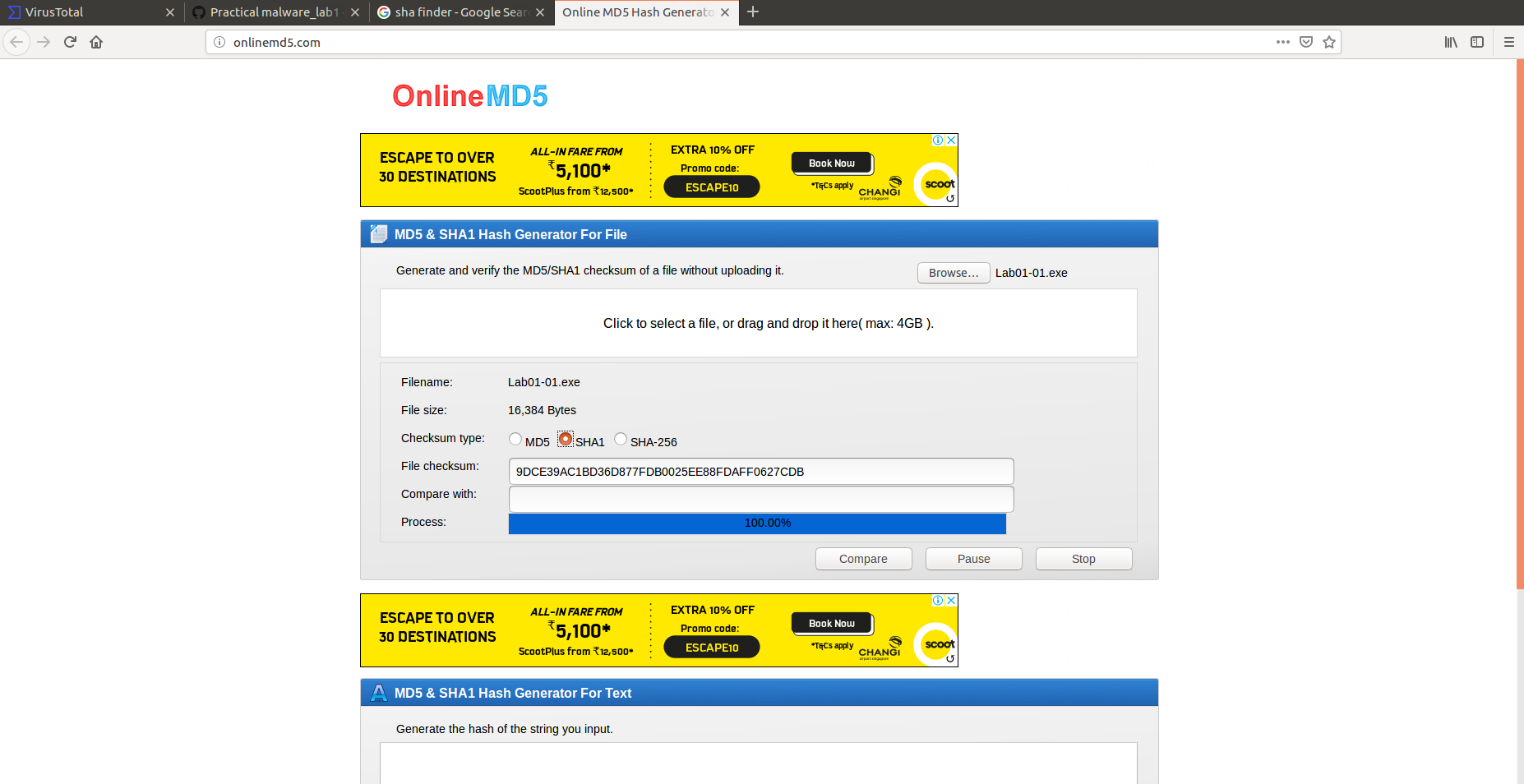
Also we can use the Hash value to find the malware. Hash value will be used to identify the files uniquley.
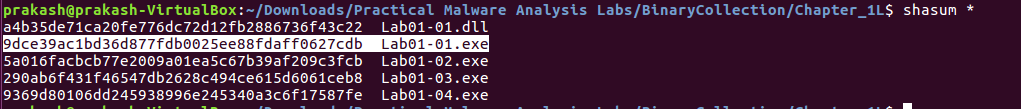
You can see the sha value of the file is always same. Hence it can be used across malware researcher to share the malware files.
String Finder
A string is a sequence of characters. When a executable try to connect to a external environment or copies a message it will contains a string in it.
finding that specific string will helpful in analysing the malicious program.
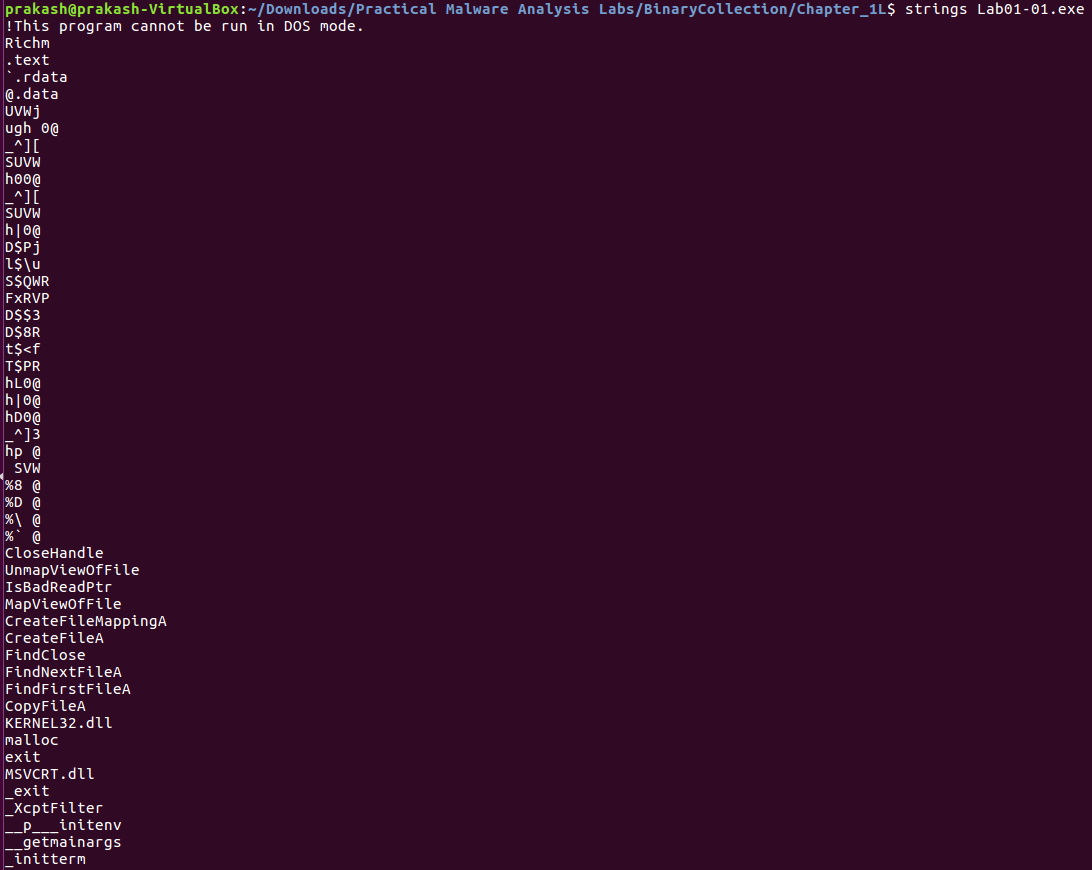
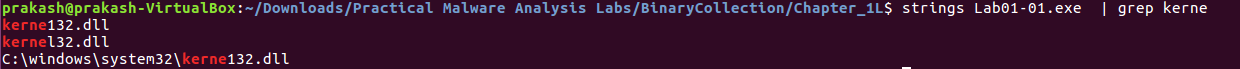
If we’re searchin for specific string in a exe it is possible to find that string using the command grep
Packed and Obfuscated Malware
Obfuscated programs contains unknown or gibberish code which makes the malware analyst confuse. It is sometimes possible that legitimate code also obfuscated to protect the source code from the users.
Packed programs are compressed programs. It limits your analysis on the suspicious executable.
Packed and obfuscated codes will often use `LoadLibrary` and 'GetProcAddress` to load and gain access to additional functions