Nmap
Hi,
In the world of hacking and malware analysis it is useful to know about the tools which make your work less and find the information about target in less amount of time.
One of such tool is Nmap - Network Mapper.
It is used to analyse the open ports, guessing the OS, accurate packet routes
There are wide range of scan types present in Nmap:
| S.No | Scan Type | Description |
|---|---|---|
| 1. | SYN Scan sS | Default Scan, Quiter than TCP connect, Send a SYN Packet and monitor the SYN ACK packet, Half-open connection on target |
| 2. | TCP connect sT | Completes the TCP handshake and makes full connection, Noisy, More load |
| 3. | Ping Sweep sP | Pinging all ports and find the open port. ICMP used to find the port. Faster for full port scan. Not accurate |
| 4. | UDP Scan sU | Used to check UDP listening ports. Used to find trojan horses and hidden RPC services |
| 5. | FIN Scan sF | Stealthy scan like SYN. False positive and negative becuase most sytemt dont send RST packet |
| 6. | NULL Scan sN | Stealthy scan that sets all TCP header flags to off or null. Not a valid packet hence unreliable results |
| 7. | XMAS Scan sX | Similiar to null scan but TCP header flags are on |
| 8. | Bounce Scan b | Uses a vulnerability in FTP protocol and scan the internal network. If FTP server that is attached to the local LAN then you can use this. |
| 9. | RPC Scan | Find RPC services. It is good to use this scan to find RPC services. Remote commands can be run in RPC. |
| 10. | Windows Scan | Relies on anamoly in response to ACK packets in some OS reveal ports that are supposed to be filtered |
| 11. | Idle Scan | Super stealthy scan. Scan packets are bounced off an external host |
Nmap commands
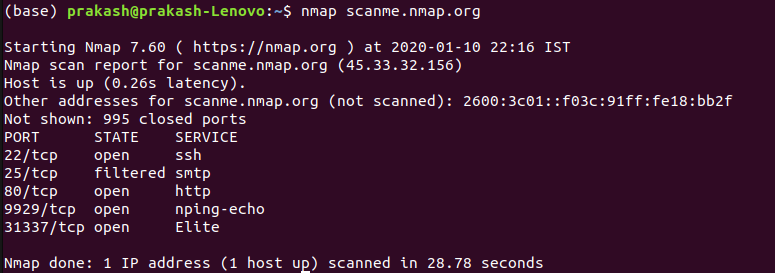
Basic command
nmap scanme.nmap.org
nmap 45.33.32.156
![1 namp basic command]()
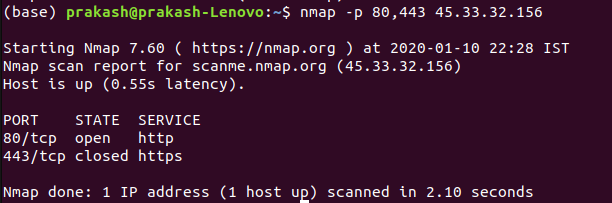
Scan specific or entire port on local or remote server
nmap -p 1-65535 scanme.nmap.org
nmap -p 80,443 scanme.nmap.org
![2 port scan]()
Scan Multiple IP address
nmap 1.1.1.1 8.8.8.8
nmap -p 1.1.1.1,2,3,4Most Common Ports
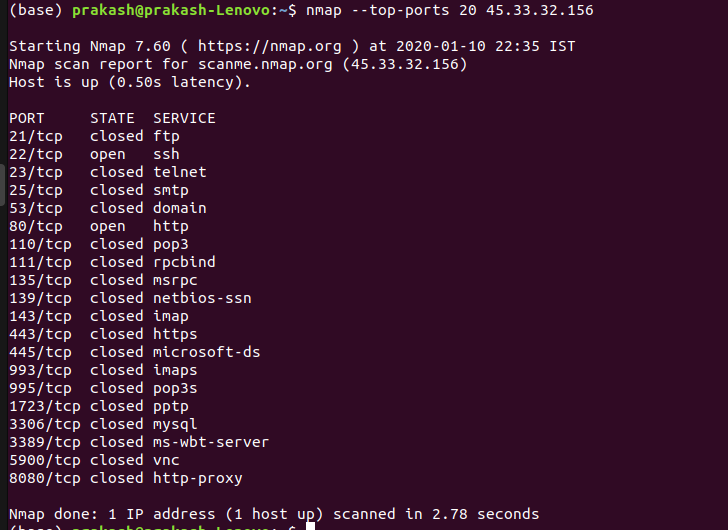
nmap --top-ports 45.33.32.156
![top20 nmap ports]()
Scan host and Ip address from a text file
nmap -iL list.txt
Note:
nmap on linux will take more time if it does not have root privileges, since it is unable to create raw sockets without it. On windows however there are no such restrictions and nmap would be fast enough.
$ sudo nmap -sP 192.168.1.1-255
-n option will tell nmap to disable dns resolution, and this would speed up the scan further.
$ sudo nmap -sP 192.168.1.1-255 -n
Use the max-rtt-timeout to speed up the scan further.
$ sudo nmap -sP 192.168.1.1-255 -n --max-rtt-timeout 50ms
Reference : https://medium.com/@infosecsanyam/nmap-cheat-sheet-nmap-scanning-types-scanning-commands-nse-scripts-868a7bd7f692
https://medium.com/@avirj/nmap-tcp-syn-scan-50106f818bf1
https://www.edureka.co/blog/nmap-tutorial/