We can access the AWS environment via UI dashboard or also via Command Line Interface. Following were the list of command line and its usage on the AWS.
To access the UI environment we shoud know the username and password of the account. And for CLI based access we should have the Access key ID and Secret Access Key.
In VAPT engagements we could found the Access key and Secret key in the developer’s repository, page source code, google dorks. In short most of the time the sensitive datas are leaked due to misconfiguration.
Aws CLI key configuration
To access the command line interface of AWS, we should need to have the AWS CLI package, it could be installed via stable package of your base machine or using the official AWS CLI repository(https://github.com/aws/aws-cli).

List users in a AWS account
aws iam list-users
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
{
"Users": [
{
"Path": "/",
"UserName": "prakash",
"UserId": "AIDA4GTIUABCD47ELANC",
"Arn": "arn:aws:iam::831234560498:user/identity",
"CreateDate": "2023-01-01T18:58:49+00:00"
},
{
"Path": "/",
"UserName": "student",
"UserId": "AIDA4GTIUDEFGHIXHYW5Q",
"Arn": "arn:aws:iam::831234560498:user/student",
"CreateDate": "2022-11-23T21:00:43+00:00"
}
]
}
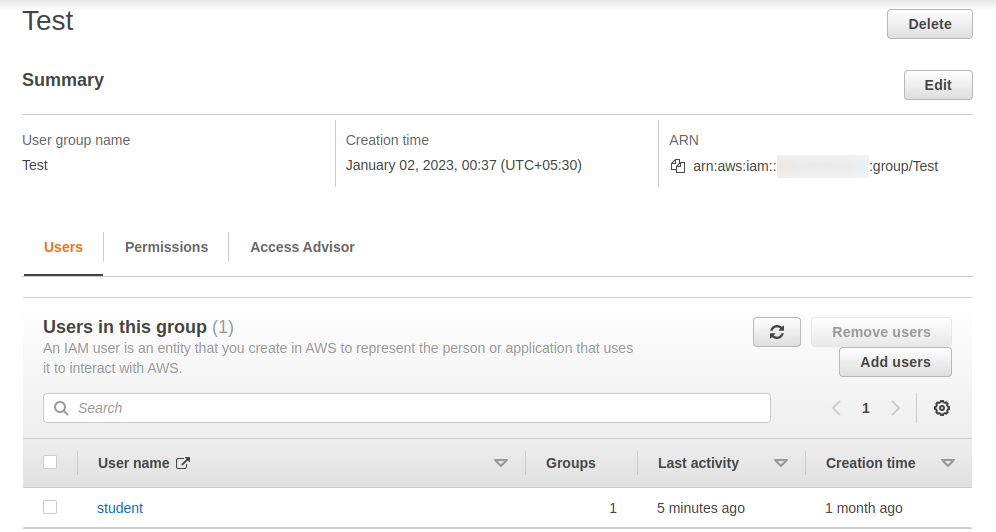
Creating a new group in UI and viewing those information in CLI
Here we could see that a group called Test is created and the student is assigned to this group
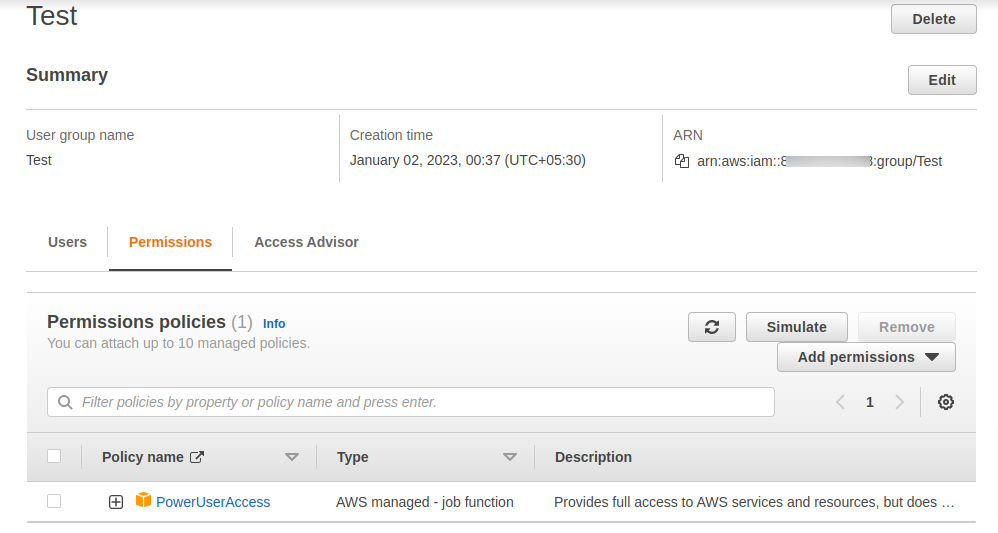
Further we assigned the Policy called PowerUserAccess
CLI to list groups of user
aws iam list-groups-for-user --user-name student
1
2
3
4
5
6
7
8
9
10
11
{
"Groups": [
{
"Path": "/",
"GroupName": "Test",
"GroupId": "AGPA4GTIUKO123NIW2EXD",
"Arn": "arn:aws:iam::831234560498:group/Test",
"CreateDate": "2023-01-01T19:07:43+00:00"
}
]
}
CLI to list policies attached to user
aws iam list-attached-user-policies --user-name student
1
2
3
4
5
6
7
8
{
"AttachedPolicies": [
{
"PolicyName": "AdministratorAccess",
"PolicyArn": "arn:aws:iam::aws:policy/AdministratorAccess"
}
]
}
CLI to list policies attached to group
aws iam list-attached-group-policies --group-name Test
1
2
3
4
5
6
7
8
{
"AttachedPolicies": [
{
"PolicyName": "PowerUserAccess",
"PolicyArn": "arn:aws:iam::aws:policy/PowerUserAccess"
}
]
}
CLI to list Groups
aws iam list-groups
1
2
3
4
5
6
7
8
9
10
11
{
"Groups": [
{
"Path": "/",
"GroupName": "Test",
"GroupId": "AGPA4GTIUKOZOONIW2EXD",
"Arn": "arn:aws:iam::838811800498:group/Test",
"CreateDate": "2023-01-01T19:07:43+00:00"
}
]
}